The development of mobile apps is nowadays on the rise. Global businesses and organizations are adopting this technology to improve customer communications and boost employee productivity. Today, these mobile apps are a requirement for any business. Even businesses that in the past never used apps are now joining this market.
Most importantly, smartphone applications are now an integral part of everyone’s lives and are even used to convey critical information. The good thing is that mobile apps have filled many aspects of our lives with ease and convenience. And the bad thing is that as mobile apps become more popular, they become more vulnerable to hackers.
Now, as mobile apps gain popularity and demand for mobile app development rises, these apps become more vulnerable to potential attacks. Many attacks have been directed at some of the most widely used apps today, which perform financial transactions, upload sensitive data, and link with personal information.
So, mobile app security needs to come first when launching a new app in the world of mobile apps, where hacking, data leaks, and criminality are more common than ever.
Apps today are capable of a wide range of tasks, including carrying out financial transactions and uploading private health information. So, personal data is thus increasingly vulnerable to misuse and theft.
To safeguard these mobile apps while enjoying their remarkable benefits, we will now outline security risks and mobile app security checklist, for app developers to refer to while building them.
What are the security risks associated with mobile applications?
The security of mobile apps is more prevalent than you might have imagined. Let’s talk about some common application security threats and mobile app security vulnerabilities you need to be aware of.
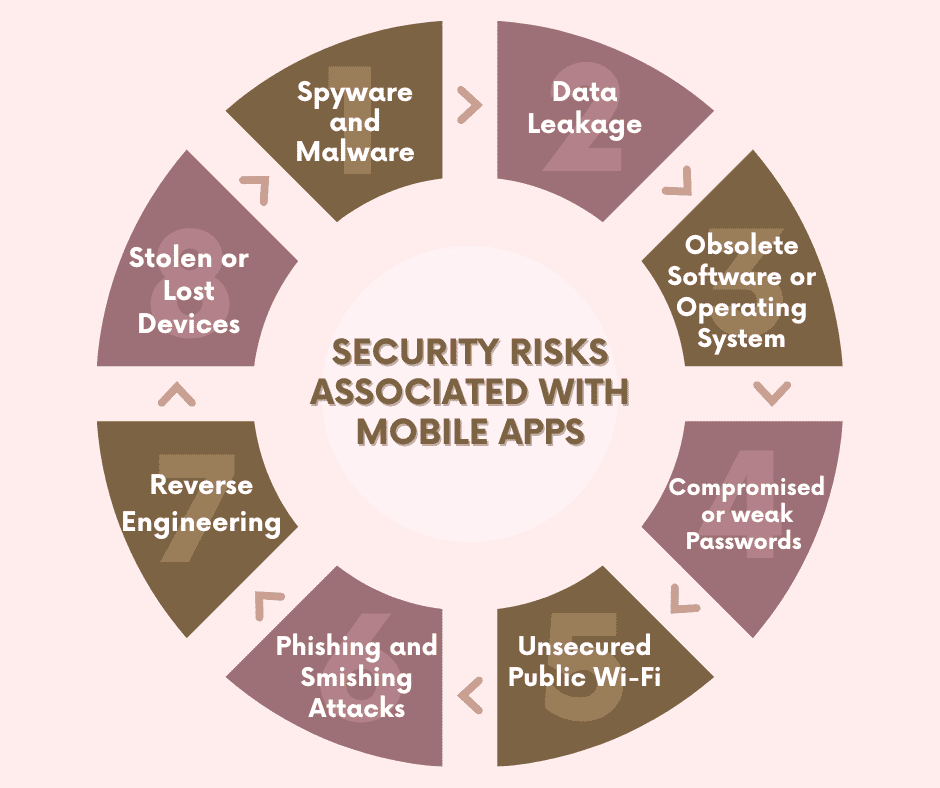
1) Spyware and Malware
Mobile devices are often set up to only allow the installation of applications from authorized app stores (e.g., Google Play or Apple Store).
Androids support third-party app stores other than iOS. So, Android developers need to be aware of this, more than iOS developers.
Once malicious software has been downloaded and installed, it may compromise all other apps on the user’s device, including those that were downloaded from reliable sources.
2) Data Leakage
Because the majority of mobile apps have minimal to no app security protection, they frequently result in unintentional data loss.
The majority of the time, when a user downloads an app, they also permit it to access other data on the device. These mobile malware programs transport sensitive data across corporate networks undetected by utilizing native distribution codes found in widely used mobile operating systems like iOS and Android.
3) Obsolete Software or Operating System
Mobile security can be compromised if you do not keep all of your software and operating systems up to date. Older software is unable to identify and stop more recent cyberattacks as malware, ransomware, and other threats become increasingly progressive.
So, you must keep your software updated, as security patches are generally included in a lot of software updates. This is valid for mobile software, mobile devices, and mobile security.
4) Compromised or weak Passwords
Passwords are currently a significant problem in our society. People just replicate the same passwords across various accounts, whether they are personal or professional accounts.
The reason for this is, there are many different tools, accounts, and subscriptions that require a password. Unfortunately, the passwords that people use repeatedly are often insecure as well.
Therefore, if one account is compromised, hackers may also have free command over other accounts too.
Also, read: Best retail apps that have helped businesses thrive during lockdown
5) Unsecured Public Wi-Fi
When Wi-Fi hot spots are accessible, nobody wants to use up all of their cellular data. And it is impossible to determine any public Wi-Fi network, who set up the network, how (or if) it’s encrypted, or who is actively accessing or monitoring it, so public Wi-Fi networks are typically less secure than private networks.
Your business may be in danger from the public Wi-Fi networks your employees use to access your servers (for example, from coffee shops or cafés). Additionally, you should never use it to access private or confidential services, such as banking or credit card details.
6) Phishing and Smishing Attacks
Mobile devices are the target of many phishing attacks since they are constantly on. Due to the lower screen sizes, email programs on mobile devices display less information, making customers more vulnerable. Additionally, mobile users are more at risk because they frequently keep an eye on their email in real-time, reading, and opening emails as soon as they arrive.
Another frequent attack is called “smishing,” which concentrates the attack on text messaging, a frequently overlooked aspect of organizational cybersecurity. The attacker sends the victim’s phone a text message that convinces them to click a link inside the message.
7) Reverse Engineering
Attackers can also attack using reverse engineering, by understanding how a mobile app function. Many apps are vulnerable to the very real risk of reverse engineering because of the nature of programming.
An attacker can find more effective ways to attack your application if they can read your code.
Using reverse engineering, the attackers can alter the source code, reveal the encryption algorithms in use, and more.
Therefore, the code written for your mobile app poses a serious security risk and can be used against you, if not appropriately secured.
8) Stolen or Lost Devices
The potential loss or theft of mobile devices is another serious risk. To gain access to confidential data stored on a mobile device, a person having physical access to the device may attempt to get past the lock screen.
Lost and stolen devices pose a rising risk to your business as more people access your systems remotely from open spaces like cafés and coffee shops using a variety of different devices.
Also, read: 11 Reasons to create a mobile app for your online shop – and how to get started?
How to ensure the security of mobile apps?
These days, where employees often combine their business and personal interests into a single device, mobile app security issues are more important.
It is the responsibility of an app developer to ensure that any mobile application he/she creates will not compromise the security of your users.
Here are ten mobile app security best practices that will help you create secure and hack-proof applications while also guaranteeing the safety of your users and the legitimacy of your app.
1) Data and Source Code Encryption
Any time data is transferred through your app, it should always be encrypted. This specific strategy helps in preventing data theft. Therefore, no attackers could abuse it.
These kinds of threats might harm your company’s reputation. Application developers need to make sure their programs are secure enough to prevent hacking and reverse engineering attempts.
The best approach to protect your application from these assaults is to encrypt the source code, which makes it unreadable.
2) Strong High-level Authentication
Weak authentications are the most common mistake made while designing apps which leads to security breaches. The apps should be developed in a way so that only strong alphanumeric passwords are accepted.
To ensure safe usage, sensitive apps should be protected with multi-factor authentication that needs biometric authentication, such as fingerprints. The recommended approach to prevent security breaches would be to encourage users to confirm authentication.
3) Use of Updated Cryptography Techniques
There are cases where even the most popular cryptographic algorithms, such as MD5 and SHA1, often fail to match the rising security standards.
To meet your highest security needs, it is, therefore, advisable to employ the most reliable encryption techniques, such as SHA-256 and 256-bit encryption.
To ensure impenetrable protection, you should also perform manual penetration testing and threat modeling on your applications before they go live.
4) Secure Network Connections
Make sure that the app has security measures in place to prevent unauthorized access and secure data if the app uses any servers or cloud servers.
Security threats should be reviewed and examined for APIs and the servers that access them. To secure the communication path between a server and a user, you can use SSL, TLS, VPN, or HTTPS.
Also, read: Native Mobile App Development: Pros, Cons, Alternatives, and cost optimization
5) Minimize Permissions
You should always avoid giving your app too many permissions, which are even not required in all apps. Requesting access to the camera should only be done if it is necessary.
Ask your mobile application for permission if it uses contacts. Keep in mind that every permission your app requests is another connection that could be vulnerable.
6) Stay Alert with Tamper-Detection Technologies and Third-Party Libraries
You can turn on notifications using certain methods when harmful code is inserted. You need to ensure that the code will stop working if it is altered by using the temper-detection technique.
And you should also deploy structured internal repositories and employ policy controls to safeguard your system from inadvertent security issues and vulnerabilities of libraries.
9) Practice Repeated Tests – QA and Security Check
Your app security goes through an ongoing, never-ending process. When new threats emerge, you must create innovative solutions to guarantee the highest level of cyber security. Review code constantly to find any security holes, then fix them before making them available to the public.
Finding loopholes in the system is a vital need. Because these vulnerabilities could develop into real dangers that provide access to important mobile app data and functionality.
10) Build a Backup and Restore Plan
Technology is developing fast, and attackers are creating clever and smart ways to compromise mobile applications and steal critical user data.
You need to protect your apps from the severe effects of a successful breach by having a backup and restore plan. If something goes wrong, you can still access the files that were recovered from the backup.
So, it is strongly recommended that developers provide users with the option of more frequent data backups and secondary storage.
Also, read: Top mobile app marketing ideas to get your business to the next level
Conclusion
When it comes to the best practices for application security, there are undoubtedly many different points of view and perspectives among security professionals.
To make yourself a more difficult target to exploit, it is always worthwhile to be better protected than the competition and to make every effort to reduce the number of errors in your applications.
These are only a few of the many more things you can do to protect your mobile app from attacks. Your users and the reputation of your mobile app will be safeguarded if security is ensured at every stage of development.
If you want to prevent malicious hacker attacks on your business and reputation, adhere to these ten best security best practices. Plus, you should encrypt the data in your databases to keep it safe.
In this way, even if hackers gain access to it, they will not be able to utilize it in any way.
Also, read: Laravel Web App into Mobile App – Top Transformation Scenarios
FAQs (Frequently Asked Questions)
Application security is the process of finding and fixing application-level vulnerabilities. Different methods and approaches are used that aim to improve the application’s overall security.
The most common methods for hackers to access your online application are as follows:
> Authentication problems.
> Exposed sensitive data.
> Missing access control at the function level.
> A security configuration error.
> Direct object references that are not safe.
> Using vulnerable third-party components.
> Unverified forwards and redirects.
A web application’s security needs to be addressed before even beginning the development process. Your web app security strategy needs to be well-planned using the finest security techniques like data encryption and multi-factor authentication.
You must perform continuous security checks throughout the whole development process. Moreover, after your web app is live, you must continue performing regular security tests.
There is no testing procedure or tool that will eliminate all the security risks. So, teams need to use a variety of techniques, such as interactive application security testing (IAST), software composition analysis (SCA) testing tools, dynamic application security testing (DAST), and static application security testing (SAST) tools. All these tools and techniques offer better security and protection.
Mobile App Development Services
Do you want to leverage mobile technology for your business? Cynoteck is a one-stop Mobile app Development Services provider. We provide iOS and Android application development services so that you can reach your target audience on any device.