Security is a set of measure implemented to protect an application from unforeseen actions that can stop functioning of the application it can be either intentional or unintentional.
Security Testing is an integral part of Software Testing that ensures software and web applications are free from any loopholes, vulnerabilities, threats, risks that may cause a big loss to the Company/Organization, and check whether that its data and resources are protected from possible intruders. Security testing is all about finding the loopholes or unforeseen attacks to the system which might result in loss of data for the Organization/Company.
Purpose of Security Testing
The primary purpose of security testing is to spot vulnerabilities and afterward repairing them. Helps to boost the current system and make sure the system can work for an extended time. To notice loopholes which will cause loss of vital information.
OWASP Top 10 Application Security
- A1:2017-Injection
- A2:2017-Broken Authentication
- A3:2017-Sensitive Data Exposure
- A4:2017-XML External Entities (XXE)
- A5:2017-Broken Access Control
- A6:2017-Security Misconfiguration
- A7:2017-Cross-Site Scripting (XSS)
- A8:2017-Insecure Deserialization
- A9:2017-Using Components with Known Vulnerabilities
- A10:2017-Insufficient Logging & Monitoring
Is it obligatory Security to be part of Continuous Integration and Continuous Deployment
If consumer stress into Security testing additional. (For e.g. If developers square measure functioning on the payment entranceway security testing is must) Gain trust in Client/Customer.
Also, read: Jest as a popular JavaScript testing framework
Things that should be done to enhance security testing
- Security expert and Quality Engineer work together: They can work together to break the system before it goes live. That mean they have found defect at an early stage.
- Responsibility for Security testing: Review all the cases created by the Quality engineer and enhance them if needed.
- Use of the right tool: For beginners, we can use ZAP (ZED ATTACK PROXY) as it is free and open source as it is also used by the professionals, easy to use web-app pen test tool and ideal for automated security testing.
- Use the enhance automated test cases given by the security expert.
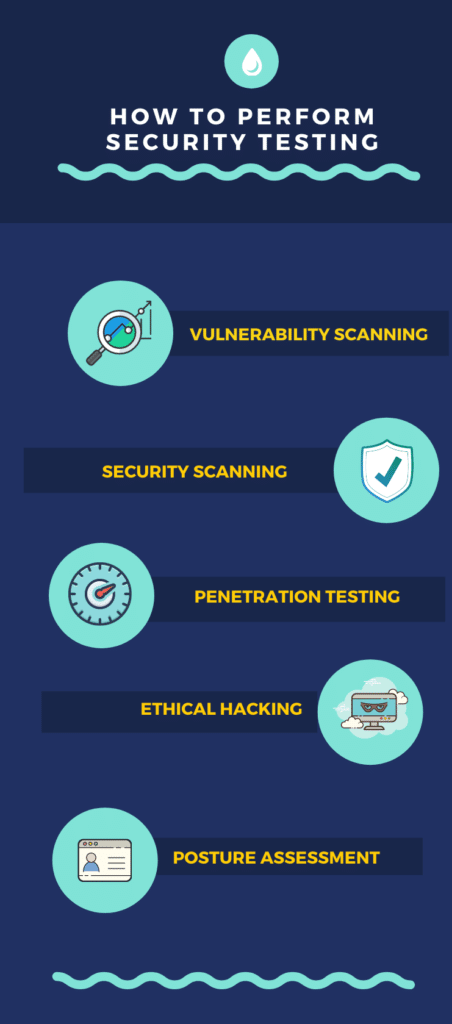
How to Perform Security Testing
- Vulnerability Scanning: It is done via Automated software to examine the framework against known exposure.
- Security Scanning: It includes dealing with system and framework weakness, finds answers to diminish the threat.
- Penetration testing: Also known as “Pen Testing or ethical hacking” it is a practice of testing computer systems, networks, or web applications to find security vulnerabilities or weaknesses that a hacker or attacker could exploit. It can be performed manually or automated with software applications.
- Risk Assessment: This kind of testing includes an examination of security dangers that are seen in the association. Risks are named as follows Low, Medium, and High. This testing prescribes controls and measures to decrease the risk.
- Security Auditing: This is often an internal investigation of Applications and Operating frameworks for security imperfections. The review should be possible as well using line by line examination of code.
- Ethical hacking: It refers to the act of vulnerabilities and locating weakness of system includes exposing a website to discover its weak points. An ethical hacker attempts to bypass system security patch that can be later exploited by the hacker or attacker.
- Posture Assessment: This joins Security checking, Ethical Hacking along with the Risk Assessments to demonstrate a general security posture of an association.
Also, read: What is smoke testing? Its Role & Benefits
Conclusion
In wrapping up our exploration into the realm of security testing, it becomes clear that it’s not just a checkbox on the development to-do list; it’s a fundamental necessity in safeguarding digital landscapes. The significance of identifying vulnerabilities before they morph into threats cannot be overstated.
As we’ve traversed the various facets of security testing, from penetration testing to code reviews, the overarching theme is one of proactive defense. The proactive stance taken through these testing methodologies instills confidence not only in the robustness of our applications but also in the trust we instill in our users.
In my experience as a Software Tester, the integration of security testing into the development lifecycle is not merely a best practice; it’s a commitment to delivering a product that stands resilient in the face of ever-evolving cyber threats. The landscape of web development is dynamic, and so must be our approach to security.
Security testing is not a one-size-fits-all solution but rather a continuous journey. The adaptability to emerging threats and the commitment to refining our security protocols are paramount. It’s not about achieving a state of absolute invulnerability but about cultivating a proactive mindset that mitigates risks effectively.
In essence, security testing is not an additional layer of complexity; it’s a shield that fortifies our digital creations. Embracing a security-first mindset is not just a trend; it’s a responsibility we shoulder as custodians of digital trust.
As we navigate the ever-evolving landscape of web development, let the ethos of security testing be ingrained in our practices. It’s not just about protecting data; it’s about fostering a digital ecosystem where users can interact with confidence and where the integrity of our creations stands unwavering.
In conclusion, let security testing be the silent guardian of our digital realms, ensuring that our web applications not only function seamlessly but also stand resilient against the unseen forces that lurk in the digital shadows.

Automated Software Testing Services
With automated testing tools like selenium, You can increase the effectiveness, efficiency and test coverage of your software application. Cynoteck technology help organizations deliver batter quality software/applications by using automated testing tools. get in touch with us for any assistance.